Technical Architecture
When your account is provisioned as a Type 1 VPC, we automatically set up and configure a virtual private cloud environment with two paired network subnets. We place this account under Emory’s parent AWS account (child/parent relationship), and apply administrative and security policies and controls that are monitored automatically with risk detectors.
We summarize the major technical components below:
- An advanced AWS at Emory account that creates a Virtual Private Cloud (VPC) that can host compute instances, servers, and databases.
- A basic AWS at Emory account that is used exclusively for bulk storage of data in the cloud. This account can be updated to an advanced account in the future.
Region
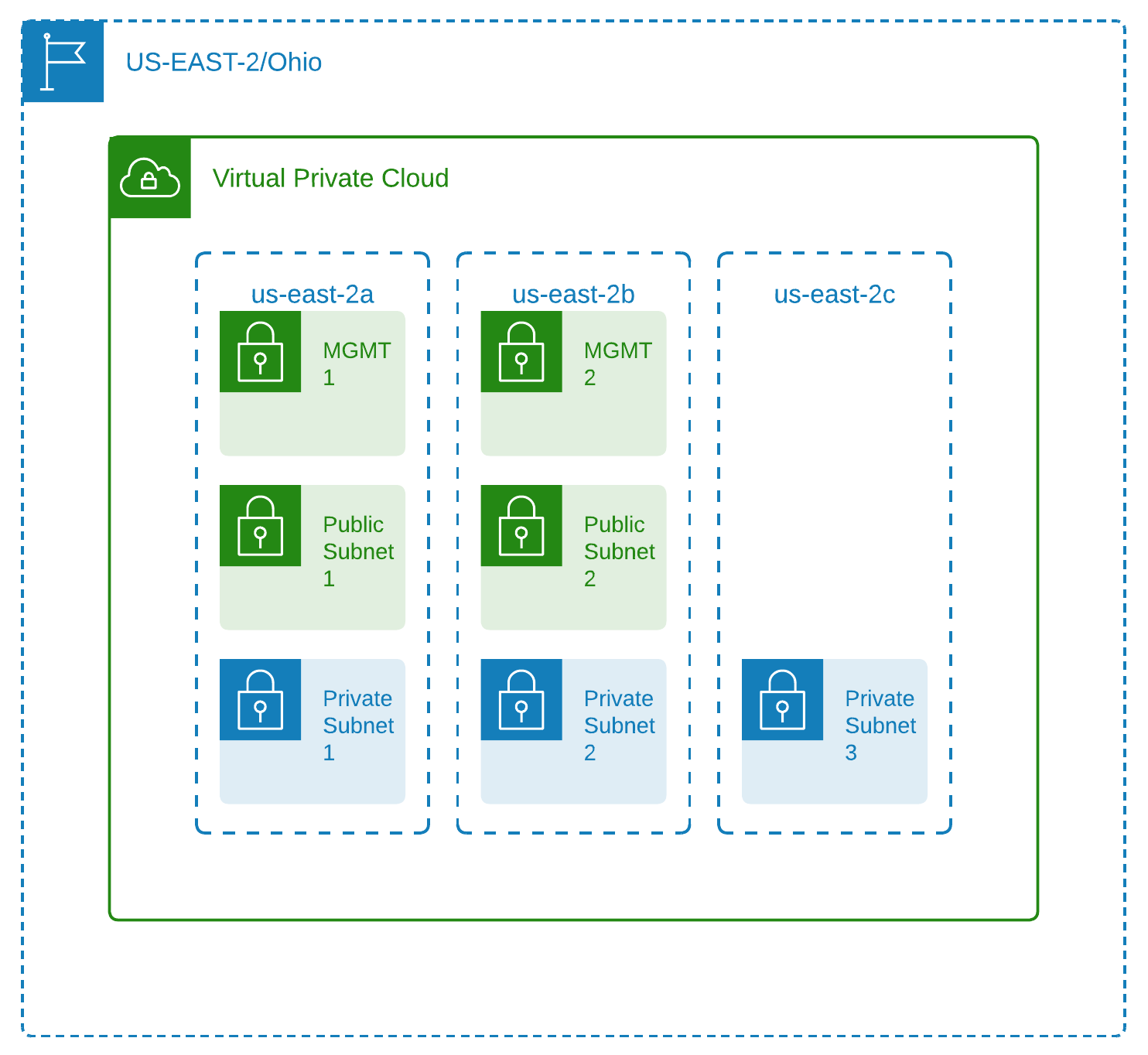
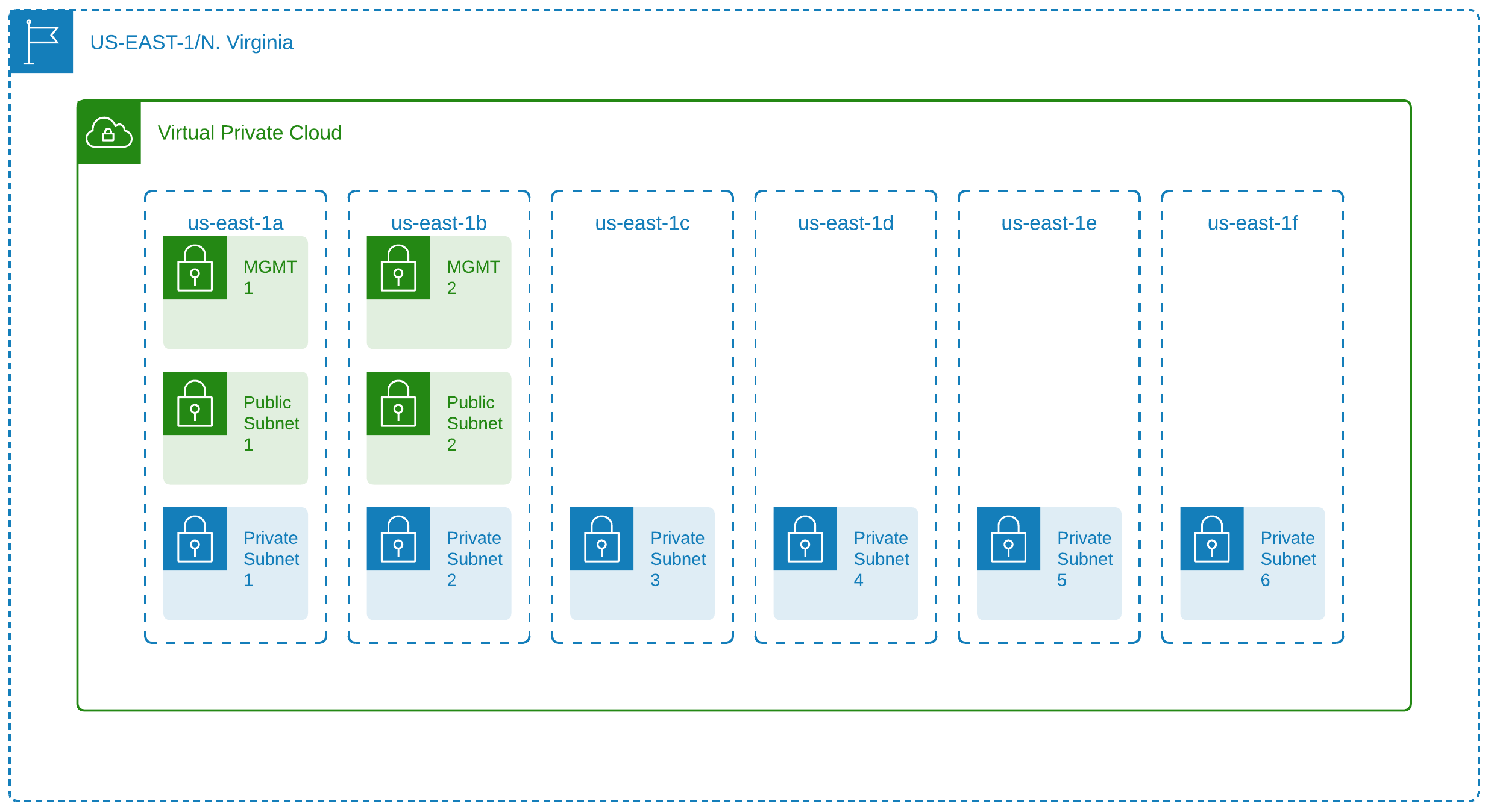
AWS maintains multiple regions around the world. Currently US-East-1 region, also known as N. Virginia, as well as US-East-2 region, also known as Ohio, are available in AWS at Emory. You will be able to pick a region when you create an account. If you wish to access other US regions, please submit a Service Now ticket.
Emory has restricted access to other regions beyond the United States due to a number of factors:
- Data stored in other countries may be subject to local privacy and security regulations and laws. By limiting the region to the United States, we limit the privacy and security constraints to US-based ones.
- In addition, in VPCs in the United States are charged in US currency. In other countries, we run risks associated with the currency conversions.
Virtual Private Cloud ( VPC)
A single Virtual Private Cloud (VPC) is automatically created when an advanced AWS at Emory account is provisioned. More VPCs may be requested and added to the account after the initial request. Each VPC acts as extensions of Emory’s network through AWS Direct Connect and AWS Transit Gateway.
Users and Roles
All AWS accounts created through an AWS at Emory account creation process are created as children accounts under an AWS at Emory parent account. This hierarchical structure gives us the ability to aggregate cost and usage information as well as enables the accounts to be eligible for enterprise support and covered by the Emory/AWS business associate agreement.
Each AWS account can have multiple users associated with it. The AWS account has an owner, generally the creator who established the account initially. Other users may be added to the account, as long as they have an active Emory NetID.
In addition, a single user may have access to multiple AWS at Emory accounts so there is a many-to-many relationship between users and AWS accounts.
All users in an AWS at Emory account inherit the Customer Administrator Role predefined by OIT. This role incorporates policies that prevent customer administrators from changing the basic network topology, security, and authorization mechanisms of the account and VPC.
Through the account creation process, the account creator will self-select the compliance class and select either HIPAA or non-HIPAA. The selection determines whether or not this account is placed in the AWS at Emory HIPAA group or an AWS at Emory Standard group. It is important to ensure this selection is accurate to ensure the appropriate controls are placed on these accounts.
Security Control Policies and Risk Detections
In order to help minimize risk in the cloud environment, all AWS at Emory accounts have a number of security control policies applied to them by default. These security control policies and associated cloud formation templates facilitate the creation of the initial environments assuring a number of best practices and security controls are in place.
To help monitor configuration changes, there are security risk detectors that check to ensure across the accounts to identify potential risks with the environments. By no means do these detectors check for all possible risks and account owners should ensure they also perform their due diligence in best security and administrative practices.
If an issue is found, the detectors will notify the account owner and account users of the issue with instructions on how to remediate them. In a few select cases, the system will perform an actual configuration change. For example, if an S3 environment is set up without encryption, the remediator will dismount the S3 environment and notify the users of the action.